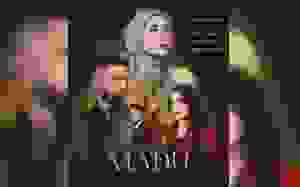Ransomware Wannacry 2017 Advisory By Mycert And Microsoft
1.0 Introduction for Ransomware Wannacry by Mycert
MyCERT is aware of the outbreak of a ransomware called as WannaCry. This ransomware is also referenced online under various names – WCry, WanaCryptor, WannaCrypt or Wana Decryptor. Ransomware is type of malware that infects computing platform and restricts users’ access until an amount of ransom is paid in order to unlock it. Victims got infected through emails that contains malicious attachment. Once the ransomware infected a system, the malware scans and infects other vulnerable systems within the network.
It exploits a vulnerability found in Windows, known as EternalBlue, that Microsoft patched in March (MS17-010). The vulnerability is in the Windows Server Message Block (SMB) service.
• https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
2.0 Impact
• Files on infected computer are encrypted and the owner is unable to access the files until a ransom of $300 worth of Bitcoin is paid.
• Individuals and organizations are discouraged from paying the ransom, as this does not guarantee access will be restored. Figure 1 shows the ransomnote found on infected computer. Figure 2 shows the text file created by the ransomware that explaining what has happened and instructions on how to pay the ransom.
• WannaCry encrypts files with the following extensions, appending .WCRY to the end of the file name:
o .lay6
o .sqlite3
o .sqlitedb
o .accdb
o .java
o .class
o .mpeg
o .djvu
o .tiff
o .backup
o .vmdk
o .sldm
o .sldx
o .potm
o .potx
o .ppam
o .ppsx
o .ppsm
o .pptm
o .xltm
o .xltx
o .xlsb
o .xlsm
o .dotx
o .dotm
o .docm
o .docb
o .jpeg
o .onetoc2
o .vsdx
o .pptx
o .xlsx
o .docx

Wannacry Ransomnote ( source from securelist.com )
3.0 Affected Product
• Unpatched Windows Vista, Windows Server 2008, Windows 7, Windows Server 2008 R2, Windows 8.1, Windows Server 2012, Windows 10, Windows Server 2012 R2, Windows Server 2016.
4.0 Recommendations
Users of this product are advised to review and patch the vulnerability described in MS17-010: https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
Users are advised to take the following preventive measures to protect their computer from ransomware infection:
a) To immediately installed the security update MS17-010 as soon as possible.
b) Disable SMBv1 on all systems and utilize SMBv2 or SMBv3 after appropriate testing.
c) Run all software as a non-privileged user (one without administrative privileges) to diminish the effects of a successful attack.
d) Block SMB traffic from all but necessary and patched systems (Firewall ports 445/139 & 3389)
e) A snort rule for ETERNALBLUE was released by Cisco as part of the "registered" rules set. Check for SID 41978 [7].
f) Emerging threats has an IDS rule that catches the ransomware activity: (ID: 2024218) [8].
g) Perform regular backups of all critical information to limit the impact of data or system loss and to help expedite the recovery process. Ideally, this data should be kept on a separate device, and backups should be stored offline;
h) Maintain up-to-date anti-virus software;
i) Keep operating system and software up-to-date regularly with the latest patches;
j) Do not follow unsolicited web links in email;
k) Be extra careful when opening email attachments;
l) Follow best and safe practices when browsing the web.
Generally, MyCERT advises the users of this software to be updated with the latest security announcements by the vendor and follow best practice security policies to determine which updates should be applied.
more info about ransomware wannacry from mycert
Artikel ini hanyalah simpanan cache dari url asal penulis yang berkebarangkalian sudah terlalu lama atau sudah dibuang :
http://www.networksecurityblogs.com/2017/05/ransomware-wannary-2017-advisory-by.html
 PING BABAB : Raksasa Aggregator Malaysia
PING BABAB : Raksasa Aggregator Malaysia
 Wannacry Ransomnote ( source from securelist.com )
Wannacry Ransomnote ( source from securelist.com )